Using Okta as an Identity Provider for Tator
This will require setting up a SAML-based application integration in Okta and then setting the SAML metadata configuration URL in Tator.
What is SAML
Security Assertion Markup Language (SAML) is a standard for sharing authentication and authorization data between an Identity Provider (IdP; in our case, Okta) and a Service Provider (SP; in our case, Tator). It is an XML-based markup language that also defines a set of protocols for communicating between the IdP and SP.
Configuring Okta
Log in to your Okta organization as an administrator and open the Applications.
Click "Create App Integration".
Select "SAML 2.0" as the Sign-in method.
Give your application a name and click next. Optional: Upload the tator app logo.
Fill in the "Single sign on URL" and "Audience URI", replacing
<DOMAIN>with your Tator domain.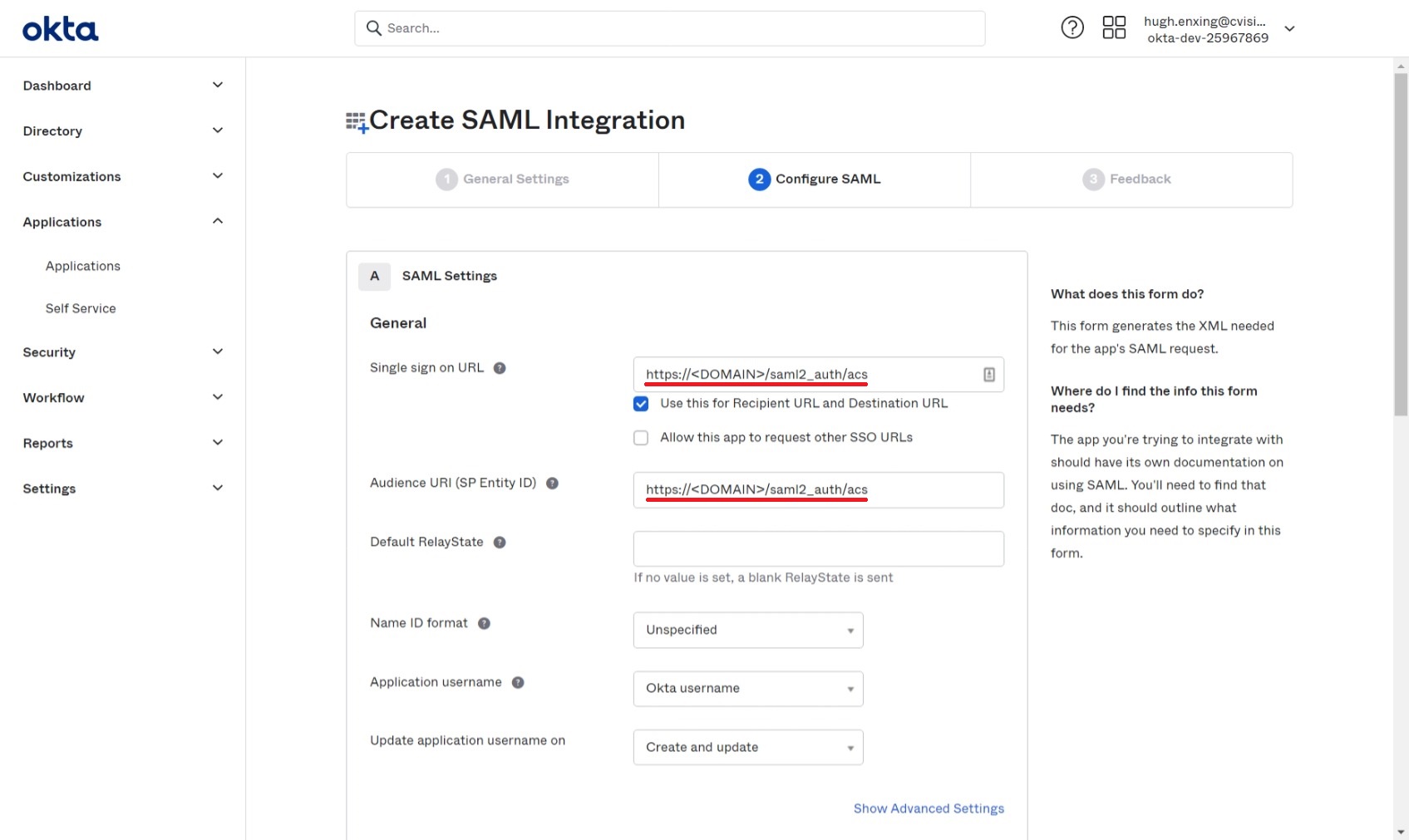
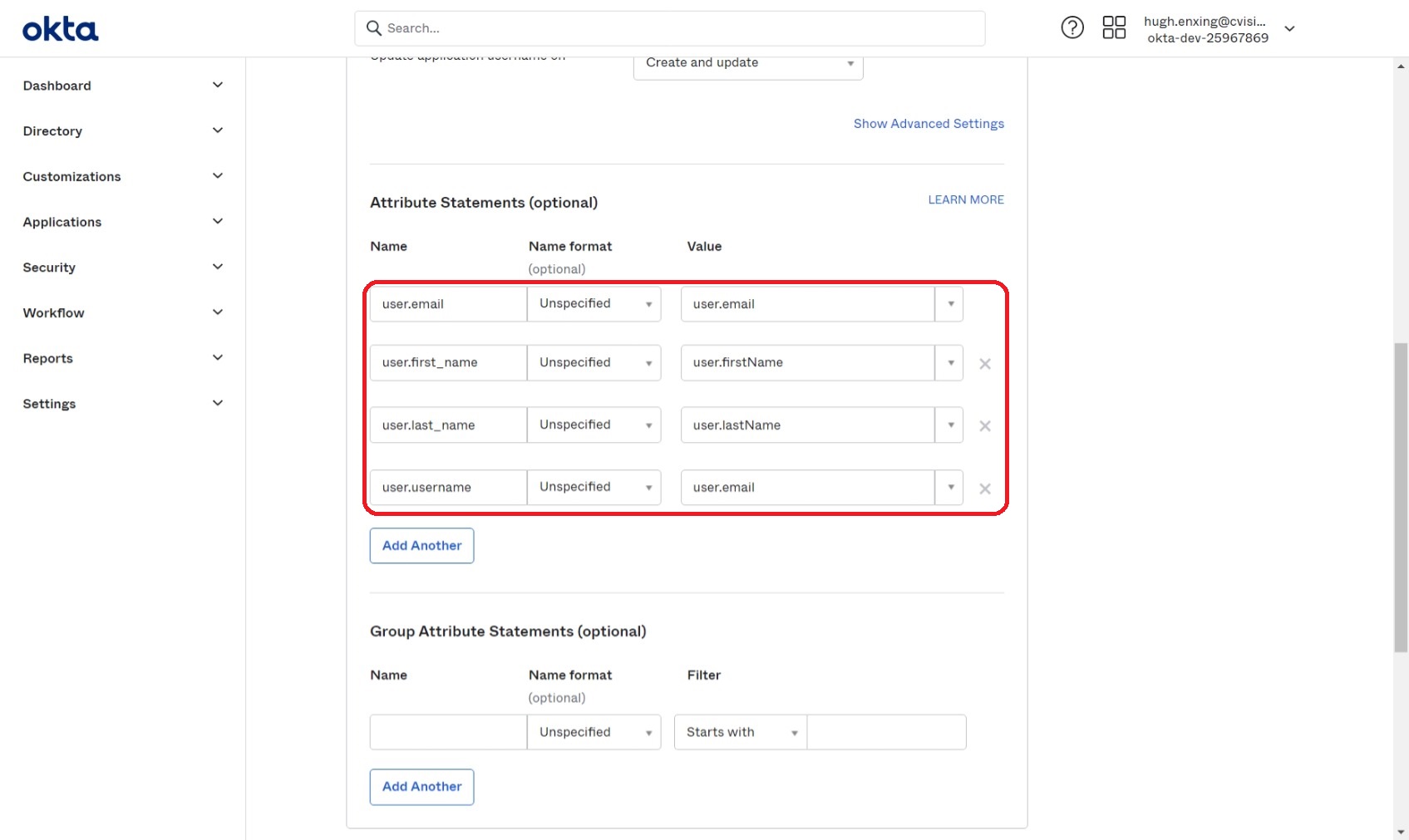
Configure the "Attribute Statements".
Click Next at the bottom of the page.
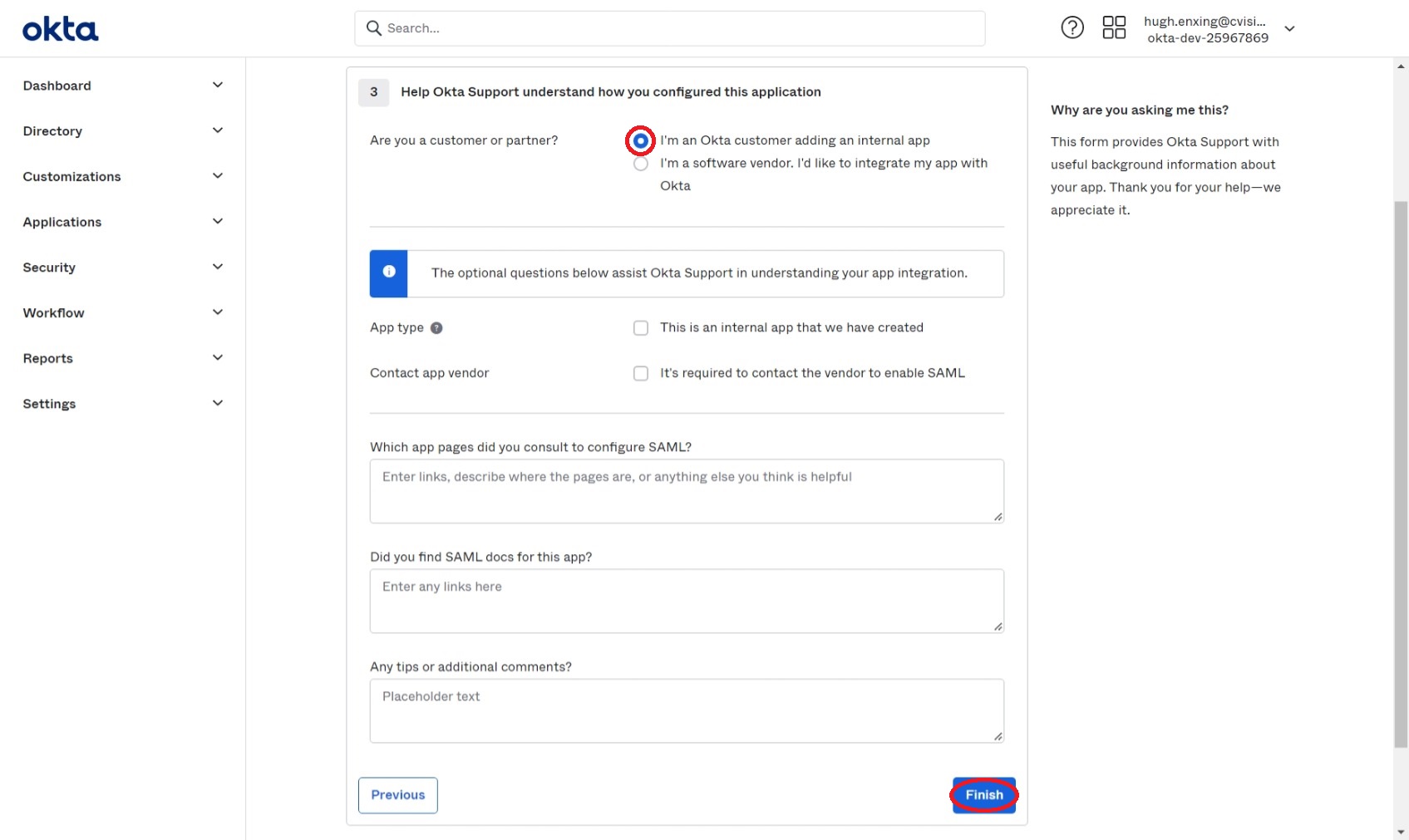
Select "I'm an Okta customer adding an internal app" and click Finish at the bottom of the page.
This will complete the creation of the integration and bring you to the Sign On tab
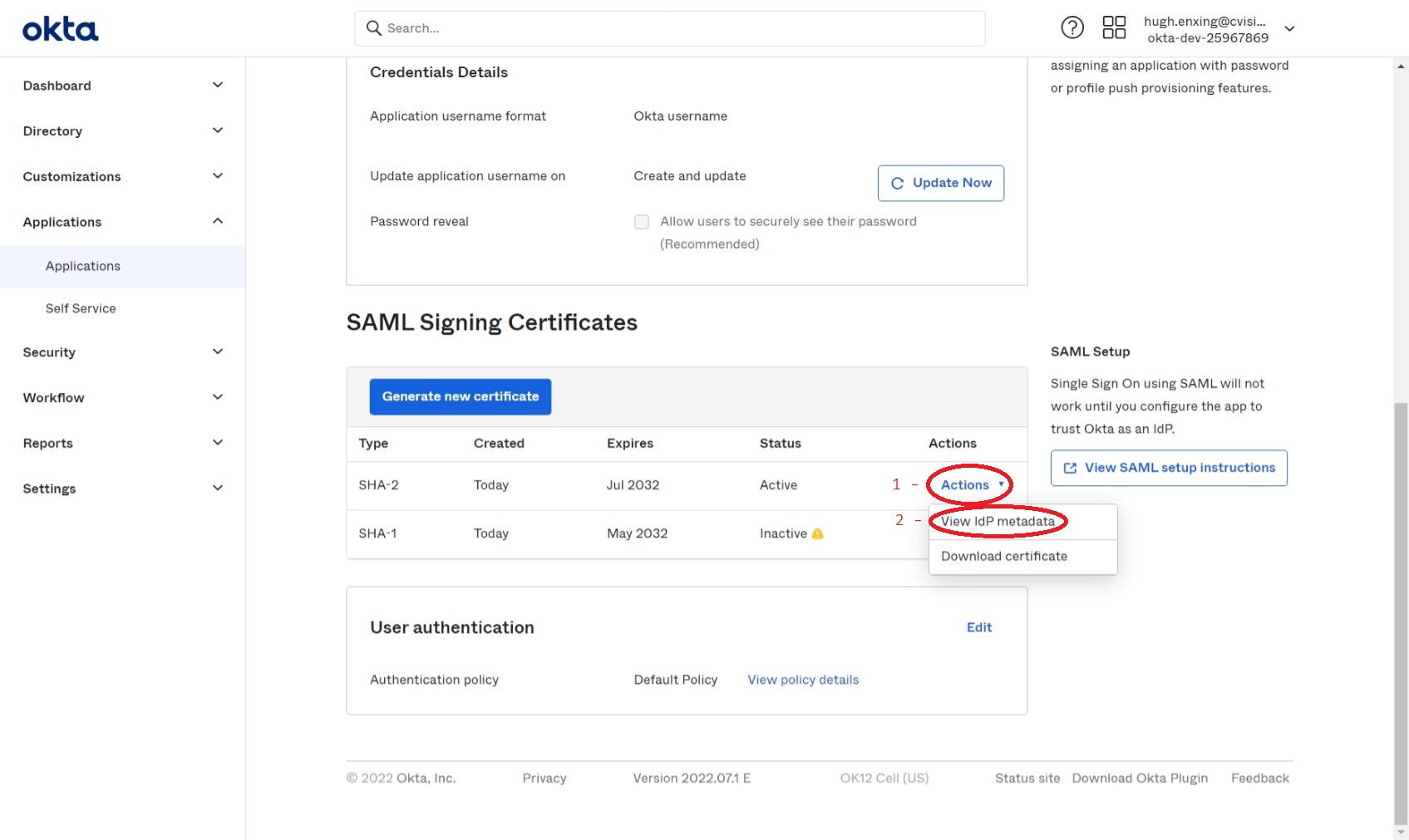
Scroll to the bottom of this page and, on the certificate marked Active, first click Actions, then right-click View IdP metadata and copy the link.
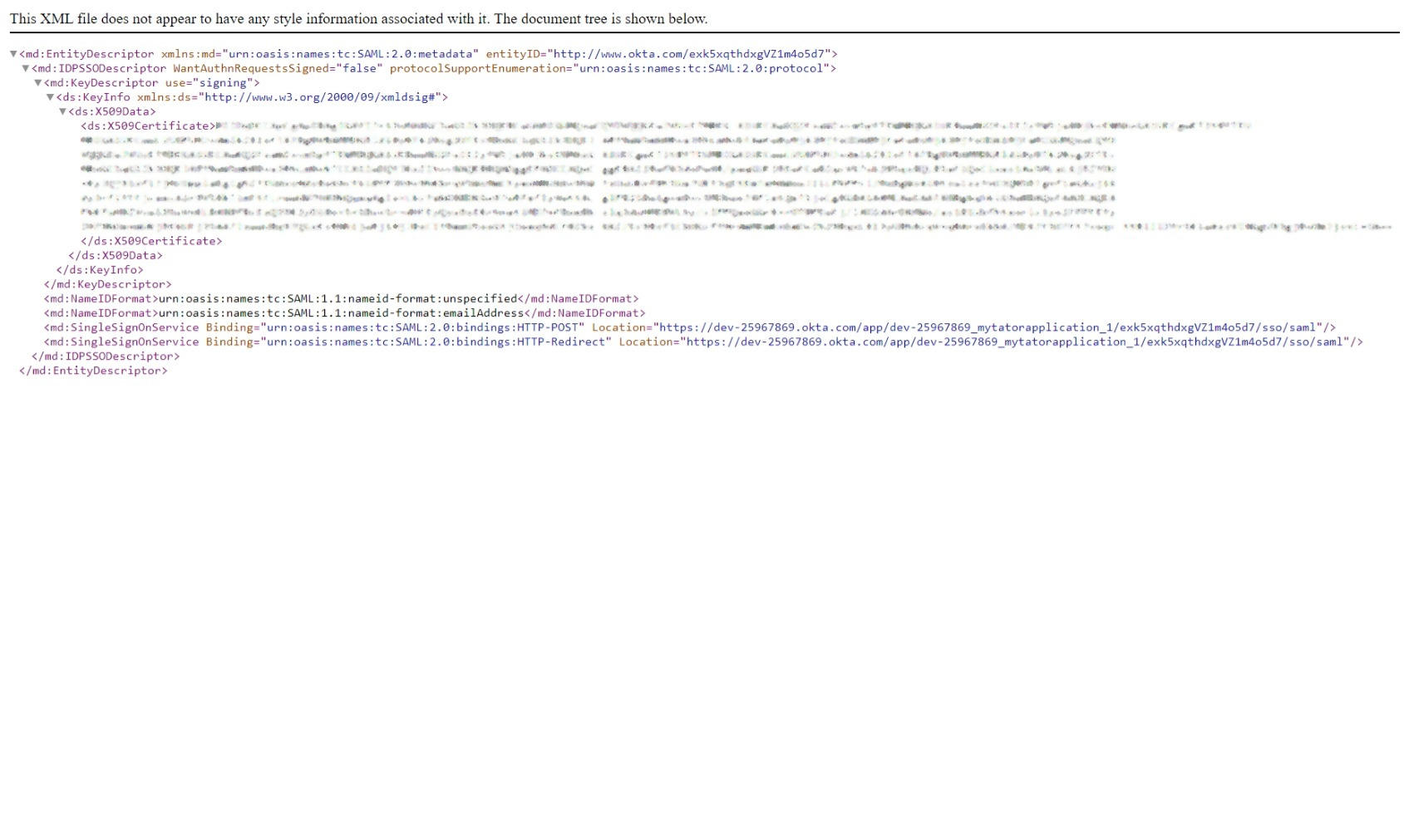
This is the link to the metadata that Tator needs to configure its side of the integration. See below for an example of what the metadata looks like. Save the link for later in this tutorial.
Configuring Tator
Open up your values.py and add the following
saml:
enabled: true
metadata_url: <URL copied from last section>
Then deploy the updated values
tator$ make cluster-update
